Actively Validated Services on Tangle Network
Tangle Network provides developers with a suite of Actively Validated Services (AVS) to power privacy-enhancing applications, cross-chain applications, and other complex cryptographically secure decentralized applications. By leveraging restaking, Tangle Network enables staked validators to provide these AVS instances to paying developers over a decentralized network.
Through these services, Tangle Network aims to achieve the following for developers:
- Reduced friction in deploying advanced decentralized applications with complex cryptographic or cryptoeconomic security requirements.
- Expanded frontier of possible application spaces through cross-chain interoperability and privacy-preserving tools.
- Simplified APIs for interacting with AVS instances and integrating them into applications.
- Outsourced computation and processing, eliminating operational burdens for developers.
Service Categories
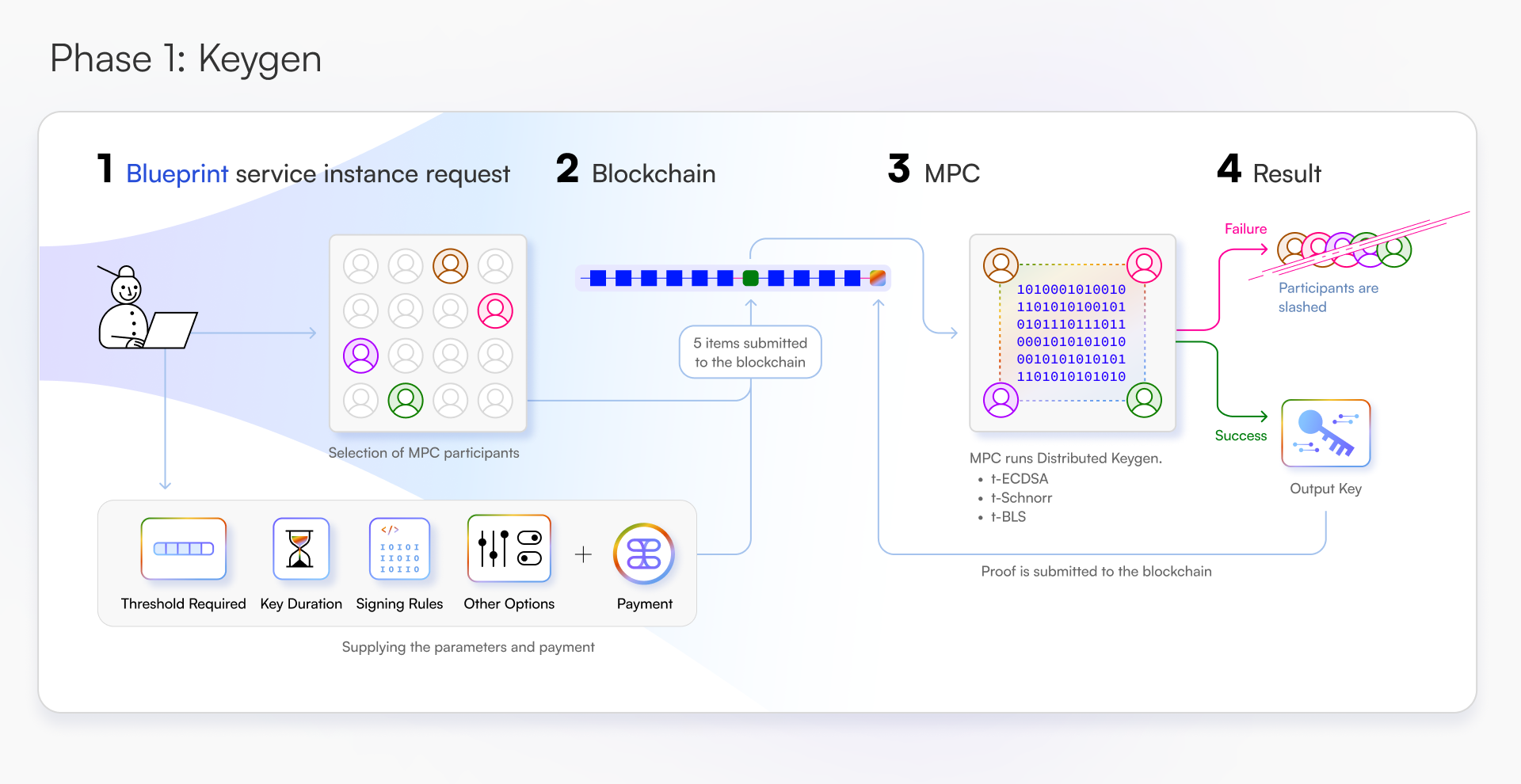
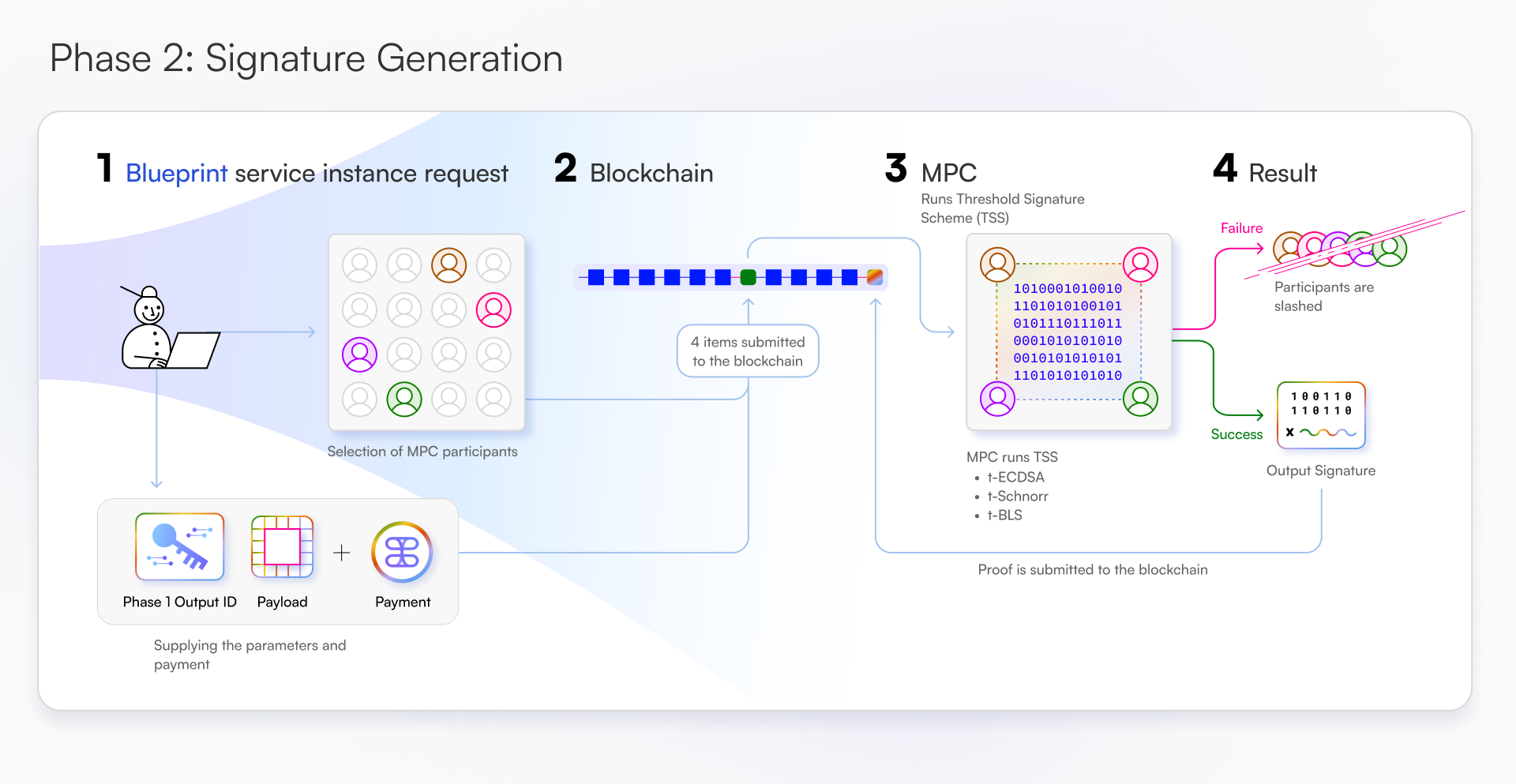
Multi-Party Computation (MPC)
Threshold signatures as a service
Signatures are pervasive in the design of blockchain bridges, oracles, and custody solutions. Tangle Network offers signature schemes as a service using threshold cryptography, enabling developers to build private and non-private cross-chain applications.
Tangle currently supports several Threshold signature schemes:
| Scheme | Description |
|---|---|
| DfnsCGGMP21Secp256k1 | ECDSA threshold signature scheme on the secp256k1 curve |
| DfnsCGGMP21Secp256r1 | ECDSA threshold signature scheme on the secp256r1 curve |
| DfnsCGGMP21Stark | ECDSA threshold signature scheme for StarkNet |
| SilentShardDKLS23Secp256k1 | Silent shard-based threshold signature scheme on secp256k1 |
| ZcashFrostP256 | FROST threshold signature scheme on the P-256 curve |
| ZcashFrostP384 | FROST threshold signature scheme on the P-384 curve |
| ZcashFrostSecp256k1 | FROST threshold signature scheme on the secp256k1 curve |
| ZcashFrostEd25519 | FROST threshold signature scheme on the Ed25519 curve |
| ZcashFrostEd448 | FROST threshold signature scheme on the Ed448 curve |
| ZcashFrostRistretto255 | FROST threshold signature scheme on the Ristretto255 group |
| GennaroDKGBls381 | BLS threshold signature scheme on the BLS12-381 curve |
Use cases for MPC services include bridges, oracles, interoperable shielded pools, and social and identity bridges.
Lifecycle
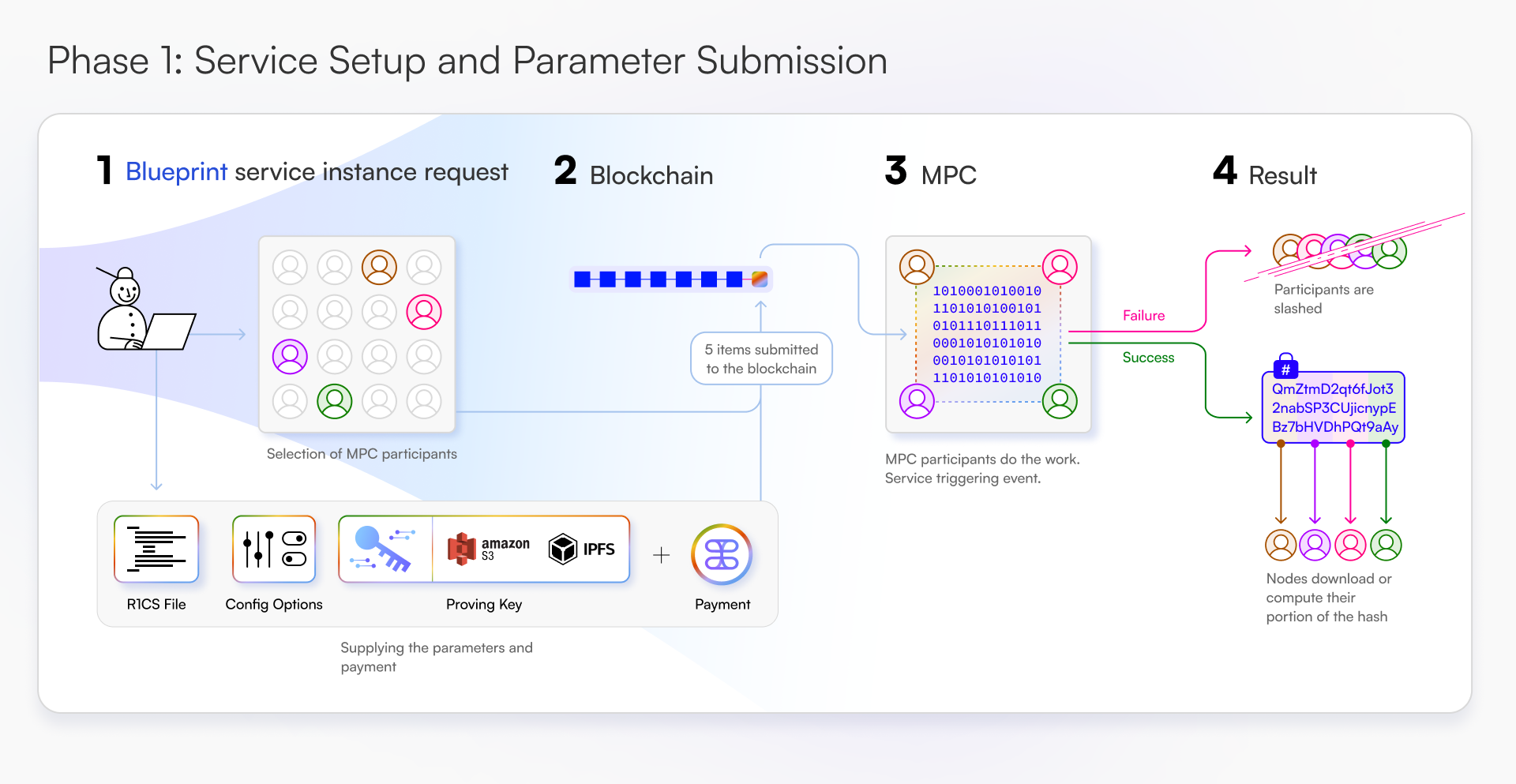
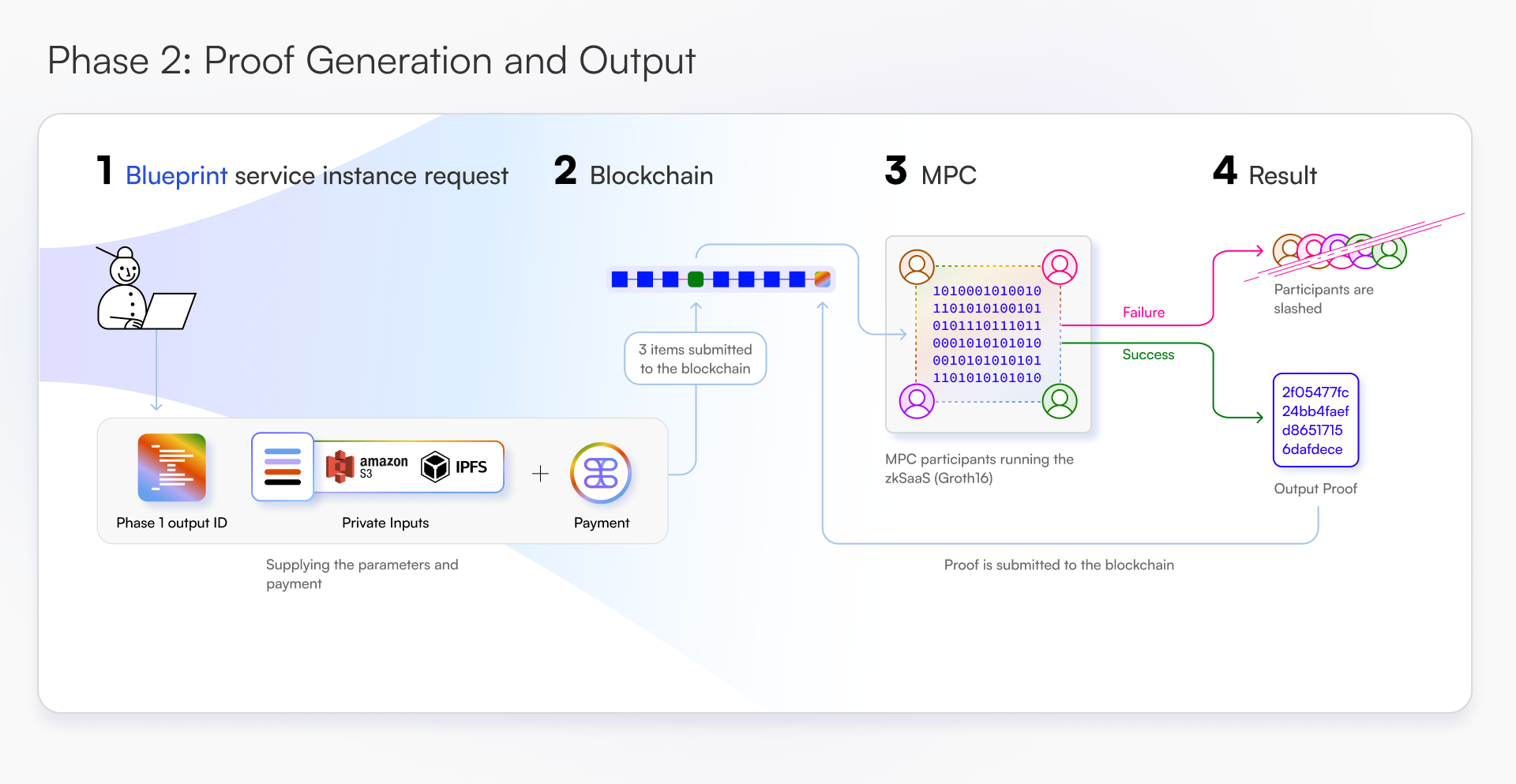
zkSNARKs as a Service (zkSaaS)
Proof generation is critical for maintaining privacy and implementation of complex cryptographic protocols within decentralized applications. Developers can build and deploy zkSaaS services allowing users to access proof generation functionality directly through the Tangle Network. This allows developers to outsource the computationally expensive tasks to a privacy-preserving infrastructure.
Tangle has built a proof of concept for zkSaaS, which can be found at https://github.com/tangle-network/zk-SaaS (opens in a new tab)
Lifecycle
Future Service Categories
We're exploring the development of new privacy technologies and AVS categories for the future:
- Bridges, oracles, prover networks
- Data storage and availability for privacy applications
- Private information retrieval as a service
- Threshold decryption as a service
- Sequencing as a service
- Randomness beacons
- zkTLS as a service
- Distributed validators as a service
- Reach out to propose more! (opens in a new tab)